


In what ways can business models of Search Engines expose users’ private information? Where? How?
How can we update the current Data Protection Regulations to improve data management and secure sensitive user data?
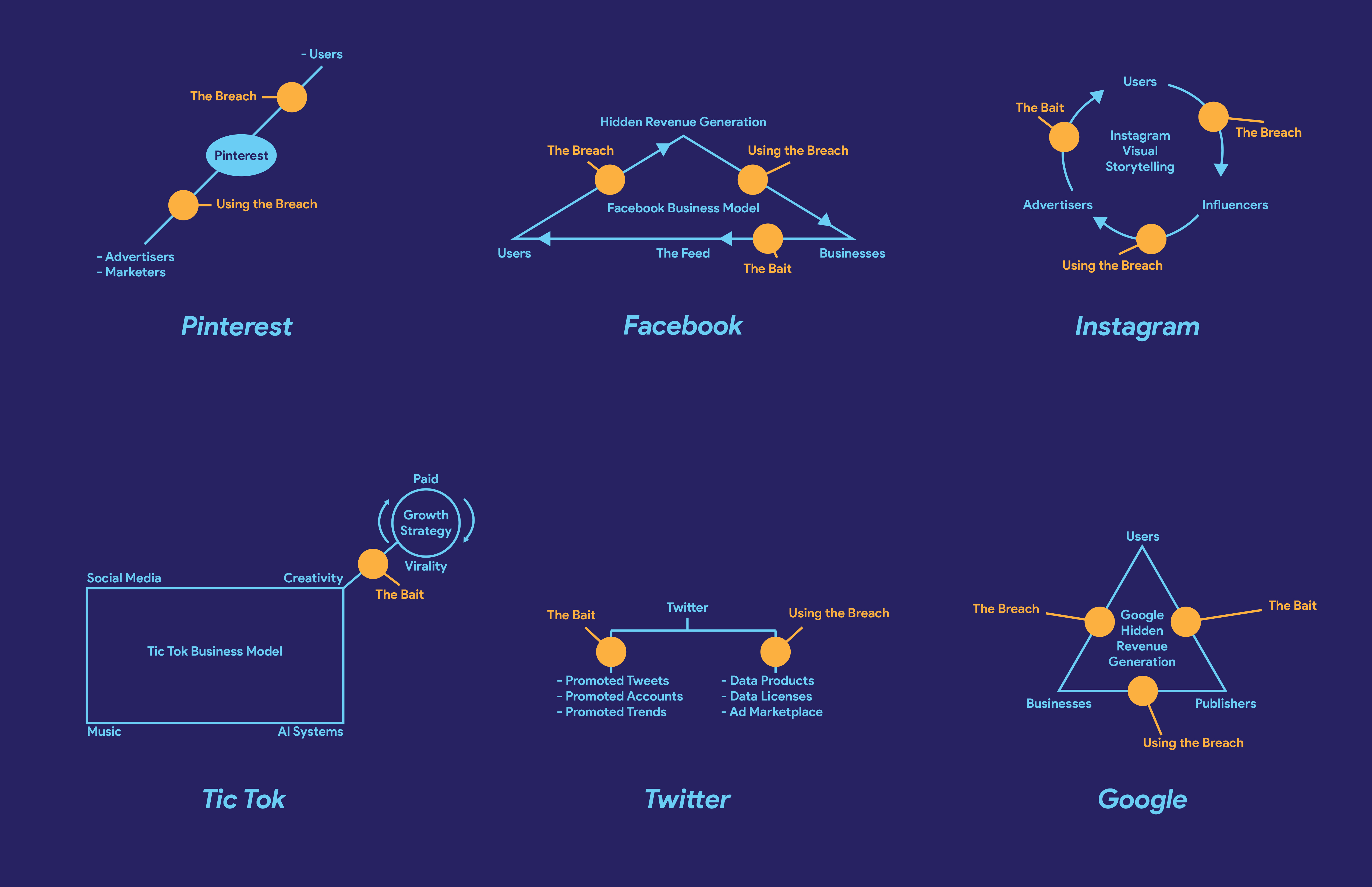
Business models of search engines such as Google’s are designed so that users believe they are offered a library of infinite resources. As users search up their desired content, their search history data are stored online and observed by corporations, in which they bid on advertisements to publishers that have the desired user demographics; as a result, users will frequently encounter advertisements that relate to their interests. The moment users’ search data is utilized by enterprises, a concept called the breach occurs, which is an opening in an online business model that allows corporations to observe and utilize stored user data to promote related businesses. The breach is possible due to the convenience of search engines and internet platforms, which is known as the bait.
Privacy is a recurring issue with the relationship between online search algorithms and users worldwide because data leaks during a breach can expose private information about users such as addresses, credit card information, or personal photos. As a result, regulations such as the General Protection Data Regulations in 2018 are implemented to address the issue; while the GDPR ensures user data is secure during a breach, the risk of data leaking through a breach is still possible, so how can the current Data Protection Regulations be updated to improve data management and further decrease the possibilities of data breaches?





My capstone proposal consists of a series of objects that will describe the elements that make up a data breach in a simpler and more digestible way. The reason for working on this capstone proposal is because describing the breach is very complex through text or word. The more practical method to describe how the components of a breach works are through imagery and symbolism.
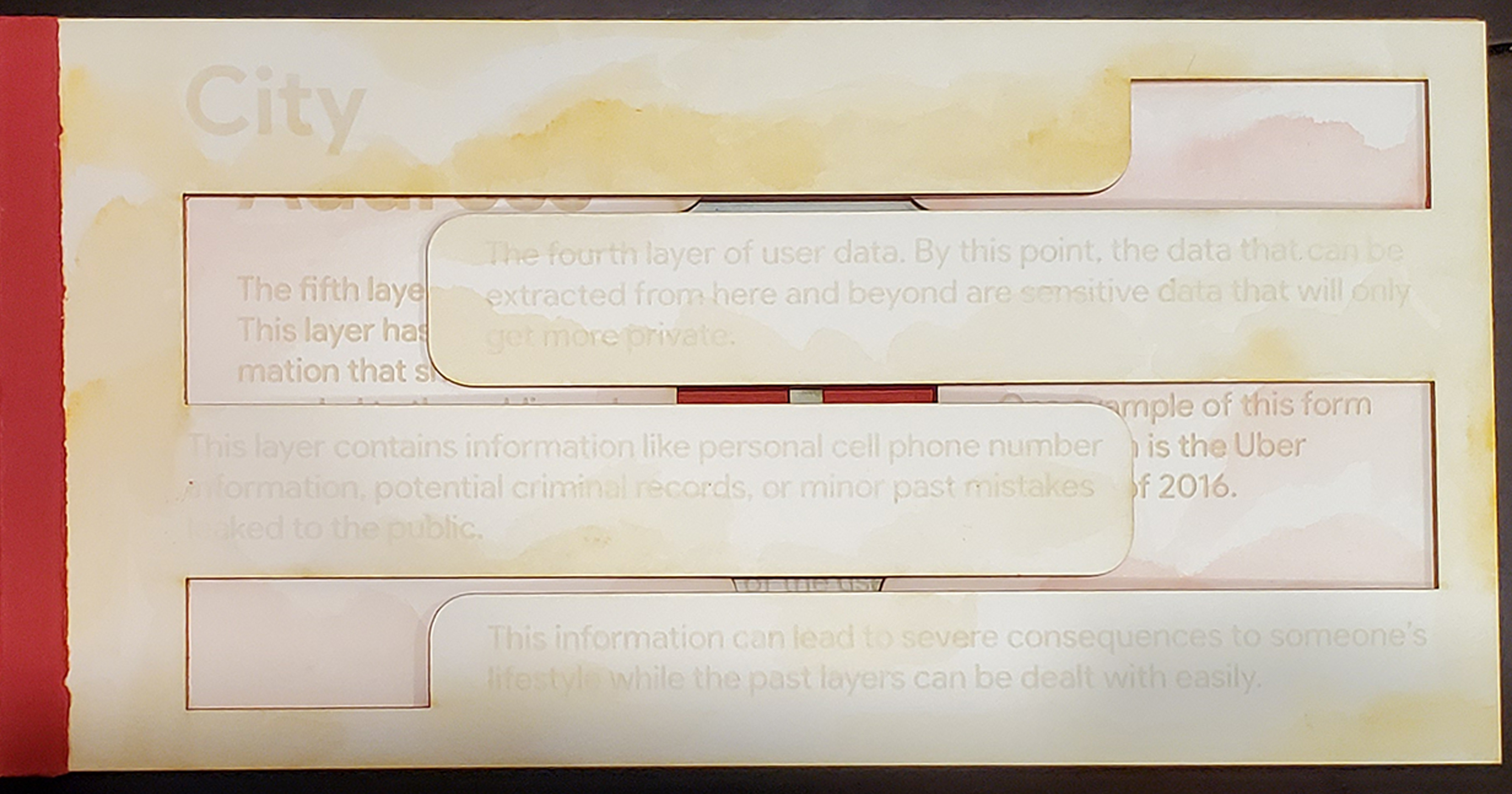
The series will be focusing on the topic of Benjamin H. Bratton’s “The Stack: On Software and Sovereignty.” The stack consists of six layers that make up how data is composed of the world. The six layers are called the User, Interface, Address, City, Cloud, and the Earth. Originally, Bratton describes the layers of the stack that each layer serves as a component for a greater whole weaved together by multiple systems. Bratton explains that as long as we can understand how each layer of the Stack works, it can serve as a key to reprogram the greater whole to be a better place. I believe Bratton’s work serves as a reference in explaining how a data breach works since a breach interrupts the symbiosis publishers, consumers, and corporations serve. If we interpret what role each Stack layer serves in the greater whole of data management, we should be able to understand the significance of data breaches. After interpreting how these layers contribute to the relationship among users, corporations, and publishers, I will find ways the Stack can be used to demonstrate how the components of a breach work such as the unbalanced hierarchy in the relationship of forms in a business model. For example, one of the sample models that I have worked on consists of five layers that compress a user’s identity in a data structure. These five layers are the interface, social media, work information, home information, and personal information. In the model, each layer has laser-cut pieces that can be extracted using tweezers. This symbolizes the way corporations and unwanted third parties extract information out of users. They do not dump out information causing a mess. They subtly extract small bits of information so it is very difficult to tell their information is being mishandled until there is too much information lost.
What I wish for users to get out of this capstone project is that viewers will be able to understand the importance and awareness of how the breach can be fatal to users, especially those whose identities are composed of the internet. Most who use the internet frequently are slightly aware that their data can be used in undesirable ways, yet there isn’t a true call to action. This project should give doubts about the information they store on the internet or how it can be stored without content so they can tread the internet much more carefully.



There was a decent reception when I displayed my work outside of Pratt Institute. According to those who have attended, the primary feedback received was that the general message was unclear on what I was striving to achieve. My Thesis Capstone is meant to be a little vague on my position because I want my audience to think and develop their own opinions about the relationship among users, publishers, and corporations. Misinformation or bias is common when it comes to understanding how data is transferred on the internet. However, the format might have resulted in being a little too unclear on what I am talking about.
To finalize everything, I will make a more simple method to digest the message in my thesis capstone by creating a 1 minute animation discussing the Stack and how it relates to User Data and the breaches involved with it. It will be published on a site like Vimeo so it is easy to access. Overall, while the information was difficult to understand through the book, it was able to make my audience think about the topic which will linger in their minds. That is considered a success because this capstone isn’t designed to make change, but meant to spread unbiased information to make the audience think for itself. As a result, the whole process from research to thesis capstone is considered a success.
According to Orberlo, there are approximately 4.33 billion users on the internet every day, which means there are 4.33 billion users with their own layers of privacy that are unaware of how their privacy is managed online. Of course, in the future, more people will become aware of how to protect themselves more efficiently when the internet gets older. It will be a matter of time when the issue of a data breach will be nullified, only for a new problem to resurface. It seems obvious to pin the blame on someone or something that users are experiencing these issues, which result in either corporations or publishers taking the blame. This is why corporations have this reputation of being greedy by taking everyone’s information and using it to their advantage. There are examples where they are at fault such as Uber’s failure to protect its users’ data in 2016, but it isn’t their fault all the time because the rise of technology leads to the rise of other openings for a data breach. Additionally, only the user is truly to blame because the user lacked the knowledge or didn’t research enough on the consequences of his or her actions. Overall, this thesis is meant to encourage users to not pin the blame on the corporation for not cleaning up their mess, but to take initiative and research their own way to prevent their own data breach.